Used for everything from accessing the internet or printing a document to downloading an attachment from an email, networks are the backbone of business today. They can refer to a small handful of devices within a single room to millions of devices spread across the entire globe, and can be defined based on purpose and/or size.
Types of Networks in Use Today
- Personal Area Network (PAN)
The smallest and most basic type of network, a PAN is made up of a wireless modem, a computer or two, phones, printers, tablets, etc., and revolves around one person in one building. These types of networks are typically found in small offices or residences, and are managed by one person or organization from a single device.
There are two types of Personal Area Network:-
- Wireless Personal Area Network: Wireless Personal Area Network is developed by simply using wireless technologies such as WiFi, Bluetooth. It is a low range network.
- Wired Personal Area Network: Wired Personal Area Network is created by using the USB.
- Local Area Network (LAN)
We’re confident that you’ve heard of these types of networks before LANs are the most frequently discussed networks, one of the most common, one of the most original and one of the simplest types of networks. LANs connect groups of computers and low-voltage devices together across short distances (within a building or between a group of two or three buildings in close proximity to each other) to share information and resources. Enterprises typically manage and maintain LANs.
Using routers, LANs can connect to wide area networks (WANs, explained below) to rapidly and safely transfer data.
- Wireless Local Area Network (WLAN)
Functioning like a LAN, WLANs make use of wireless network technology, such as Wi-Fi. Typically seen in the same types of applications as LANs, these types of networks don’t require that devices rely on physical cables to connect to the network.
- Campus Area Network (CAN)
Larger than LANs, but smaller than metropolitan area networks (MANs, explained below), these types of networks are typically seen in universities, large K-12 school districts or small businesses. They can be spread across several buildings that are fairly close to each other so users can share resources.
- Metropolitan Area Network (MAN)
These types of networks are larger than LANs but smaller than WANs and incorporate elements from both types of networks. MANs span an entire geographic area (typically a town or city, but sometimes a campus). Ownership and maintenance is handled by either a single person or company (a local council, a large company, etc.).
Uses of Metropolitan Area Network
- MAN is used in communication between the banks in a city.
- It can be used in an Airline Reservation.
- It can be used in a college within a city.
- It can also be used for communication in the military.
- Wide Area Network (WAN)
Slightly more complex than a LAN, a WAN connects computers together across longer physical distances. This allows computers and low-voltage devices to be remotely connected to each other over one large network to communicate even when they’re miles apart.
The Internet is the most basic example of a WAN, connecting all computers together around the world. Because of a WAN’s vast reach, it is typically owned and maintained by multiple administrators or the public.
Advantages of Wide Area Network
Following are the advantages of the Wide Area Network:
- Geographical area: A Wide Area Network provides a large geographical area. Suppose if the branch of our office is in a different city then we can connect with them through WAN. The internet provides a leased line through which we can connect with another branch.
- Centralized data: In case of WAN network, data is centralized. Therefore, we do not need to buy the emails, files or back up servers.
- Get updated files: Software companies work on the live server. Therefore, the programmers get the updated files within seconds.
- Exchange messages: In a WAN network, messages are transmitted fast. The web application like Facebook, Whatsapp, Skype allows you to communicate with friends.
- Sharing of software and resources: In WAN network, we can share the software and other resources like a hard drive, RAM.
- Global business: We can do the business over the internet globally.
- High bandwidth: If we use the leased lines for our company then this gives the high bandwidth. The high bandwidth increases the data transfer rate which in turn increases the productivity of our company.
Disadvantages of Wide Area Network
- Security issue: A WAN network has more security issues as compared to LAN and MAN network as all the technologies are combined together that creates the security problem.
- Needs Firewall & antivirus software: The data is transferred on the internet which can be changed or hacked by the hackers, so the firewall needs to be used. Some people can inject the virus in our system so antivirus is needed to protect from such a virus.
- High Setup cost: An installation cost of the WAN network is high as it involves the purchasing of routers, switches.
- Troubleshooting problems: It covers a large area so fixing the problem is difficult.
- Storage-Area Network (SAN)
As a dedicated high-speed network that connects shared pools of storage devices to several servers, these types of networks don’t rely on a LAN or WAN. Instead, they move storage resources away from the network and place them into their own high-performance network. SANs can be accessed in the same fashion as a drive attached to a server. Types of storage-area networks include converged, virtual and unified SANs.
- System-Area Network (SAN)
This term is fairly new within the past two decades. It is used to explain a relatively local network that is designed to provide high-speed connection in server-to-server applications (cluster environments), storage area networks (called “SANs” as well) and processor-to-processor applications. The computers connected on a SAN operate as a single system at very high speeds.
- Passive Optical Local Area Network (POLAN)
As an alternative to traditional switch-based Ethernet LANs, POLAN technology can be integrated into structured cabling to overcome concerns about supporting traditional Ethernet protocols and network applications such as PoE (Power over Ethernet). A point-to-multipoint LAN architecture, POLAN uses optical splitters to split an optical signal from one strand of singlemode optical fiber into multiple signals to serve users and devices.
- Enterprise Private Network (EPN)
These types of networks are built and owned by businesses that want to securely connect its various locations to share computer resources.
- Virtual Private Network (VPN)
VPN stands for virtual private network. A virtual private network (VPN) is a technology that creates a safe and encrypted connection over a less secure network, such as the internet. Virtual Private network is a way to extend a private network using a public network such as internet. The name only suggests that it is Virtual “private network” i.e. user can be the part of local network sitting at a remote location. It makes use of tunneling protocols to establish a secure connection.
Type of VPN (Virtual Network Protocols)
Internet Protocol Security (IPSec)
We can make use of this protocol for encryption. It is used as a protocol suite. It is used as a “protocol suite for securing Internet Protocol (IP) communications by authenticating and encrypting each packet of IP of a data stream.” It requires expensive, time-consuming client installations, which is its most significant disadvantage.
Point-to-Point Tunneling Protocol (PPTP)
Generally, it is the most widely used VPN protocol among windows users. It was created by Microsoft in association with the other technology companies. The most significant disadvantage of PPTP is that it does not provide encryption. It relies on PPP (Point-to-Point Protocol). It is implemented for the security measures. It is also available for Linux and Mac users. As compared to other methods, PPTP is faster.
Layer 2 Tunneling Protocol (L2TP)
It is another tunnelling protocol which supports VPN. L2TP is created by Microsoft and Cisco as a combination between PPTP and L2F (Layer 2 Forwarding). L2TP also does not provide encryption as like as PPTP. The main difference between both of them is that L2TP delivers data confidentiality and data integrity.
Secure Socket Layer (SSL)
It is a VPN accessible via https over a web browser. Its most significant advantage is that it doesn’t need any software installed because it uses the web browser as the client application. With the help of SSL VPN, the user’s access can be restricted to specific claims instead of allowing access to the whole network.
Privacy, Security and Encryption
Data sent across the public Internet is generally not protected from curious eyes, but you can make your Internet communications secure and extend your private network with a virtual private network (VPN) connection. VPN uses a technique known as tunneling to transfer data securely on the Internet to a remote access.
The Internet connection over the VPN is encrypted and secure. New authentication and encryption protocols are enforced by the remote access server. Sensitive data is hidden from the public, but it is securely accessible to appropriate users through a VPN.
VPN and its legality
Using VPN is legal in most of the countries, the legality of using a VPN service depends on the country and its geopolitical relations with another country as well. A reliable and secure VPN is always legal if you are not intended to use for any illegal activities like to commit a fraud online, cyber theft, or in some countries to download copyrighted content.
China has decided to block all VPN (Virtual private networks by next year, as per report of Bloomberg. Many Chinese Internet users use VPNs to privately access websites that are blocked under China’s so called “great firewall”. This is done to avoid any information leakage to rival countries and so as to tighten the information security.
Characteristics of a Computer Network
- Share resources from one computer to another.
- Create files and store them in one computer, access those files from the other computers connected over the network.
- Connect a printer, scanner, or a fax machine to one computer within the network and let other computers of the network use the machines available over the network.
NODA
A node is any physical device within a network of other tools that’s able to send, receive, or forward information. A personal computer is the most common node. It’s called the computer node or internet node.
Modems, switches, hubs, bridges, servers, and printers are also nodes, as are other devices that connect over Wi-Fi or Ethernet. For example, a network connecting three computers and one printer, along with two more wireless devices, has six total nodes.
Nodes within a computer network must have some form of identification, like an IP address or MAC address, for other network devices to recognize it. A node without this information, or one that’s offline, no longer functions as a node.
In telecommunications networks, a node is either a redistribution point or a communication endpoint. The definition of a node depends on the network and protocol layer referred to. A physical network node is an electronic device that is attached to a network, and is capable of creating, receiving, or transmitting information over a communications channel. A passive distribution point such as a distribution frame or patch panel is consequently not a node.
Network nodes are the physical pieces that make up a network. They usually include any device that both receives and then communicates information. But they might receive and store the data, relay the information elsewhere, or create and send data instead.
For example, a computer node might back up files online or send an email, but it can also stream videos and download other files. A network printer can receive print requests from other devices on the network, while a scanner can send images back to the computer. A router determines which data goes to which devices that request file downloads within a system, but it can also send requests out to the public internet.
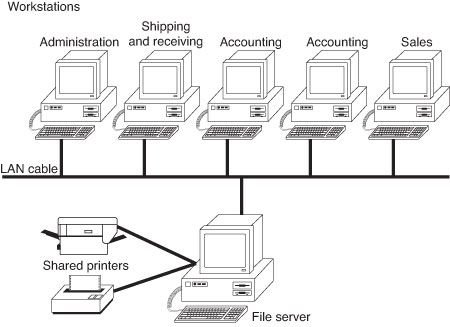
Client Server LAN
On a client/server network, every computer has a distinct role: that of either a client or a server. A server is designed to share its resources among the client computers on the network. Typically, servers are located in secured areas, such as locked closets or data centers (server rooms), because they hold an organization’s most valuable data and do not have to be accessed by operators on a continuous basis. The rest of the computers on the network function as clients.
The components of a client/server LAN.